Browser Scope Has Merged With Aussie Hosting
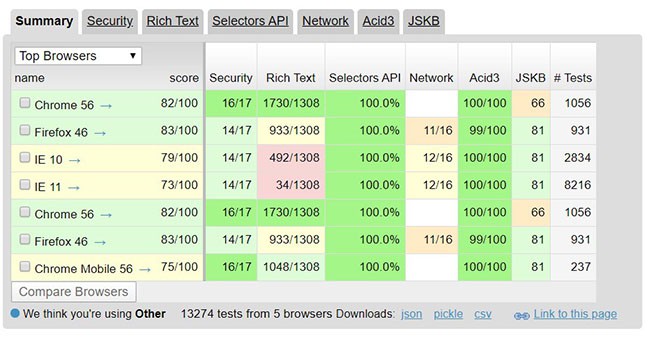 On Jan 21st of 2020, BrowerScope has joined forces with Aussie Hosting.
On Jan 21st of 2020, BrowerScope has joined forces with Aussie Hosting.
Browserscope is a community-driven project for profiling web browsers.
The goals are to foster innovation by tracking browser functionality and to be a resource for web developers.
Unfortunately as of late 2019 BrowserScope was unable to pay for the increasing server costs of their tool being used by thousands of daily users. Nathan Finch of Aussie Hosting offered to maintain the domain and upgrade the the set of browser tools available.
The original functionality of Browser Scope as an open source tool for profiling web browsers has been expanded to also provide a quite of additional tools including:
- ☑️ Browser security testing
- ☑️ CSS versions
- ☑️ Browser compatibility
- ☑️ Version checks
- ☑️ 3rd party tracking settings
Nathan has also added a robust set of security testing parameters to the original project. Detailed below:
What are the Security Tests?
This page contains a suite of security tests that measure whether the browser supports JavaScript APIs that allow safe interactions between sites, and whether it follows industry best practices for blocking harmful interactions between sites.
The initial set of tests were contributed by Adam Barth, Collin Jackson, Mustafa Acer, and David Lin-Shung Huang.
JSON.parse
Checks whether the browser natively supports the JSON.parse API. Native JSON parsing is safer than using eval.
toStaticHTML
Checks whether the browser supports the toStaticHTML API for sanitizing untrusted inputs.
httpOnly cookies
Checks whether the browser supports the httpOnly cookie attribute, which is a mitigation for cross-site scripting attacks.
X-Frame-Options
Checks whether the browser supports the X-Frame-Options API, which prevents clickjacking attacks by restricting how pages may be framed.
X-Content-Type-Options
Checks whether the browser supports the X-Content-Type-Options API, which prevents MIME sniffing.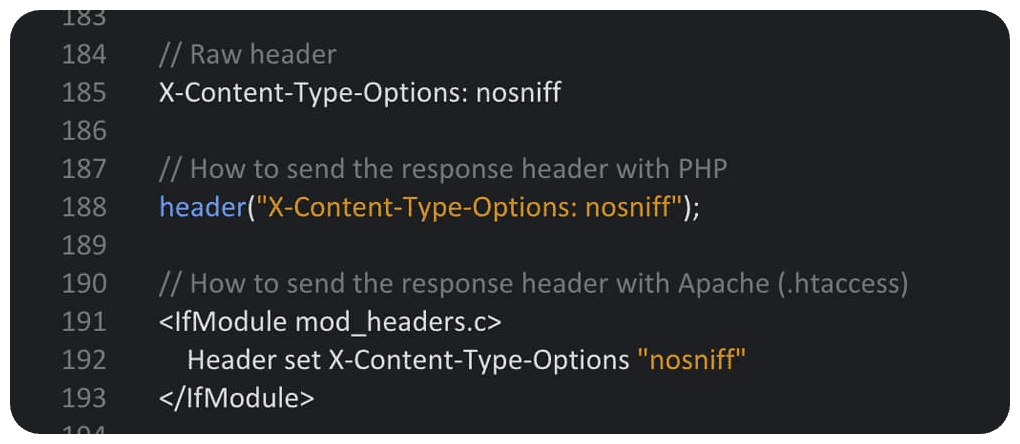
Block reflected XSS
Checks whether the browser blocks execution of JavaScript code that appears in the request URL. Browser-based XSS filters mitigate some classes of cross-site scripting attacks.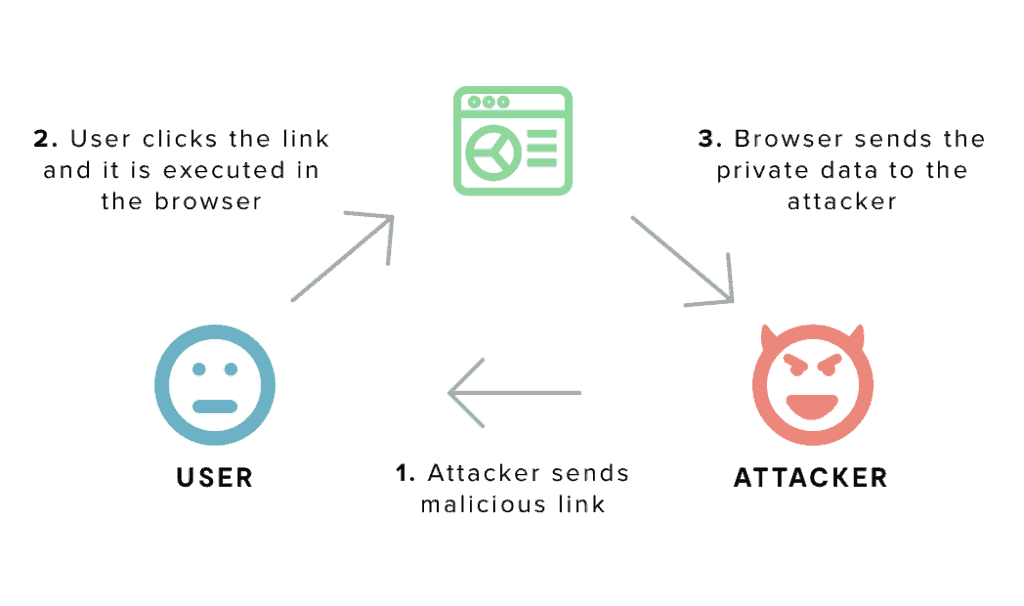
Block location spoofing
The global "location" object can be used by JavaScript to determine what page it is executing on. It is used by Flash Player, Google AJAX API, and many bookmarklets. Browsers should block JavaScript rootkits that try to overwrite the location object.
Block JSON hijacking
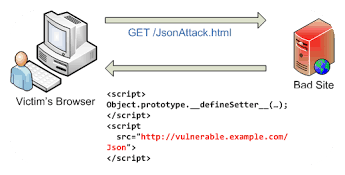
Documents encoded in JSON format can be read across domains if the browser supports a mutable Array constructor that is called when array literals are encountered.
JSON hijacking is also possible if the browser supports a mutable setter function for the Object prototype that is called when object literals are encountered.
Block XSS in CSS
Script in stylesheets can be used by attackers to evade server-side XSS filters. Support for CSS expressions has been discontinued in IE8 standards mode and XBL in stylesheets has been restricted to same-origin code in separate files in Firefox. We check to make sure that script injected into a site via stylesheet does not execute.
Sandbox attribute
Checks whether the browser supports the sandbox attribute, which enables a set of extra restrictions on any content hosted by the iframe.
Origin header
Checks whether the browser supports the Origin header, which is a mitigation for cross-site request forgery (CSRF) attacks.
Strict Transport Security
Checks whether the browser supports Strict Transport Security, which enables web sites to declare themselves accessible only via secure connections.
Block cross-origin CSS attacks
By injecting CSS selectors into the target site, attackers can steal confidential data across domains using style sheet import, even without JavaScript. Browsers should correctly determine the content type when loading cross-origin CSS resources.
Cross Origin Resource Sharing
Checks whether the browser supports the APIs for making cross origin requests.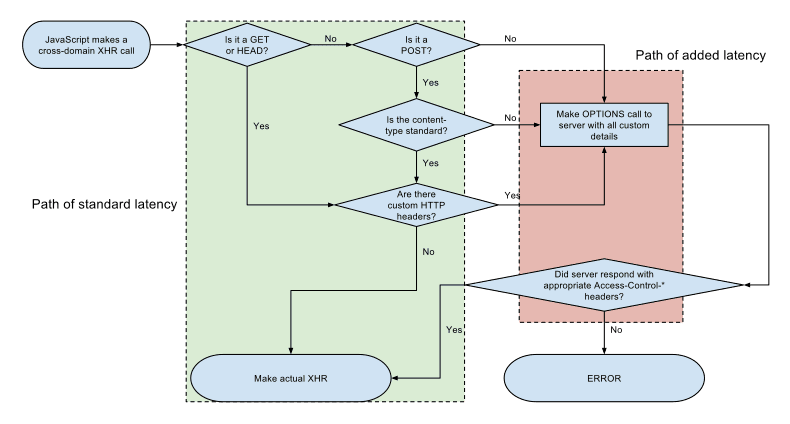
Block visited link sniffing
Most browsers display visited links with a :visited CSS pseudo class. A user's browsing history can be sniffed by testing the visited links by checking this CSS class. We test whether browsers restrict access to the :visited pseudo class.
Content Security Policy
Checks whether the browser supports Content Security Policy, which reduces the XSS attack surfaces for websites that wish to opt-in.
