What is Bullet-Proof Hosting?
While the term “bullet-proof” might seem like its a good thing, it's actually not. Security folks in the web industry use the name to refer to hosting services that are lax when it comes to what they allow their customers to upload and distribute on their websites.
More credible web hosting providers typically have stringent guidelines and a long list of rules that govern what their customers can and cannot put on their sites.
Additionally, most web hosting companies would not knowingly host hackers and malicious organizations who are intent on breaking laws or stealing both data and money. Bullet-proof hosts, however, pride themselves on providing a safe-haven to these types of criminals.
What Happens on the Bullet-proof Host Servers?
Frequently these bullet-proof web hosts are found in countries with more lenient with law enforcement of cyber-crimes.
This provides fertile ground for shady organizations and hackers alike when they know that the “don’t ask, don’t tell” approach of the host allows them to operate with impunity and free from prosecution for data theft, bribery, illegal trafficking, and extortion.
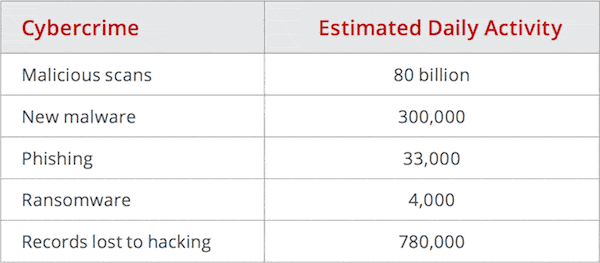
Source: McAfee / CSIS 2018 report
The main goal of a bullet-proof host is to stay online and keep their client’s data and credentials secure even if approached by law enforcement agencies. This is really where the term “bullet-proof” comes from as they present themselves as indestructible.
You’ve likely heard of bot attacks, ransomware, malware, and phishing attacks. What you may not know if there is an underground network that supports, facilitates, and hosts these hackers.
The setup of these bulletproof hosts are configured similarly to legitimate hosting companies, but they are very lenient with what they allow to be hosted on their servers.
Bullet-proof hosts take advantage of lax laws in different countries to skirt the system and profit from the underlying, illicit activities of the hackers they host.
These nefarious organizations with their lax rules and purported protection from law enforcement are a breeding ground for all that is ugly about the internet. They host hackers, criminals, and illicit content. Here’s just a taste of what you might find on a bullet-proof host’s servers.
Malware
Hackers need a home for their most profitable tools, and chief among them is the malware that helps them attack computers and websites.
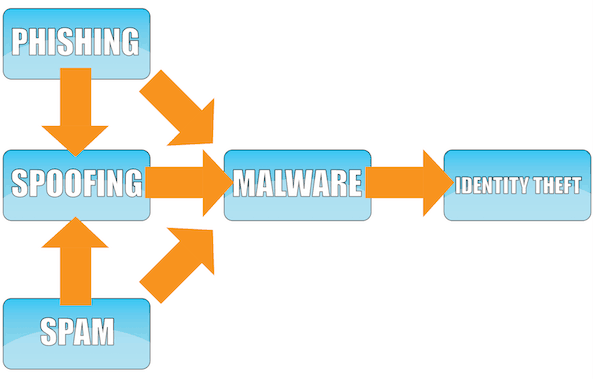
Hackers use malware to corrupt data, take over user machines, elicit ransom, and hack sites via software vulnerabilities.
Phishing is an excellent example of a hacking technique that helps malware enter a computer.
Black Market Websites
Any website that promotes illegal behavior or illicit trafficking of data, contraband, or stolen goods is likely hosted by a bullet-proof server.
These sites host unlawful gambling, child pornography, human trafficking networks, terrorists, hacking resources, stolen credit card data, drugs, fake passports, and many other black market materials and activities. If you can name an illegal or illicit activity, it likely takes place on one of these sites.
Bot Networks
Bots are another tool of hackers used to attack web servers in denial of service (DDoS) schemes where hundreds, thousands, or even millions of remote computers that have been compromised and essentially turned unknowingly into a “bot” by malware are used to crash sites.
This is another favorite tool of hackers often crashing websites and costing retailers, businesses, and organizations millions in lost revenue or traffic.
Knowledge is Power
While it might be easy enough to avoid using a bullet-proof hosting service by merely choosing a well-known, well-reviewed hosting site, that does not remove or alleviate the need for enhanced security measures. It also does not mean that the hackers dealing through bullet-proof hosts will go away.
Taking steps and the security measures will help to tighten security and keep websites safe in a day and age when it seems like attacks are coming from all sides.
The best way to combat hackers and bullet-proof hosting is to remove your website as a target and make it as secure as possible.

